Yesterday, a protocol on the Arbitrum blockchain fell victim to a hack that resulted in the loss of $7.7 million in crypto.
The attacker was able to exploit a problem involving the protocol’s internal slippage management, making a fortune in a matter of minutes.
Let’s try to delve deeper into the matter.
Jimbos, Arbitrum’s crypto protocol, hacked for 7.7 million
On Sunday, 28 May at 2:30 AM, Jimbos, a decentralized crypto protocol based on Arbitrum, was hacked for 4,090 Ether, corresponding to over $7.7 million.
The hacker was able to exploit a slippage problem in the platform to carry out a series of transactions by taking home the loot and emptying the protocol’s pools.
Slippage, for those who do not know, refers to the difference between the expected price of a transaction and the price at which it is actually executed.
This spread usually occurs when large orders are placed by whales that unbalance the relationship between two tokens in a pool, or when there is little liquidity within a decentralized market.
In this case, however, the problem with the Jimbos protocol is not about slippage per se, but rather the absence of a control measure that can limit undesirable effects.
This address, due to the flaw manifested by the system, was able to manipulate the liquidity of the protocol at a skewed price, removing 4090 Ether from the pools through a reverse swap operation.
The news was immediately noticed and reported on Twitter by Peckshield, a cybersecurity company in the web3 world, and later also announced by the official Jimbos project team
The Jimbos protocol, created not even a month ago, was intended to address the volatility of its native JIMBO token through a testing approach.
Unfortunately, the slippage vulnerability was fatal and allowed the malicious party to exploit it in its favor by altering the price of the token, which lost about 40% of its value last night.
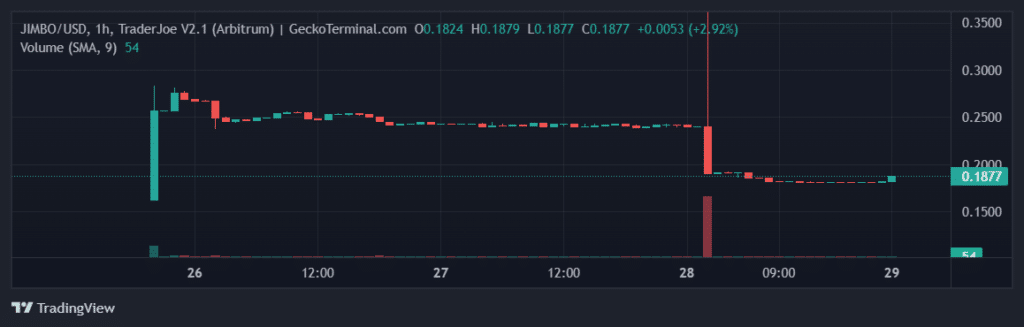
In the following chart (TraderJoe V2 market pair JIMBO-WETH) it is possible to see a large red candle, illustrative of what happened.
At 2 AM on 28 May, the candle opened with a price of $0.24, touched a high via a spike of $1808, and closed at $0.19 per token.
It is evident how the monstrous manipulation of JIMBO’s price allowed the attacker to profit.
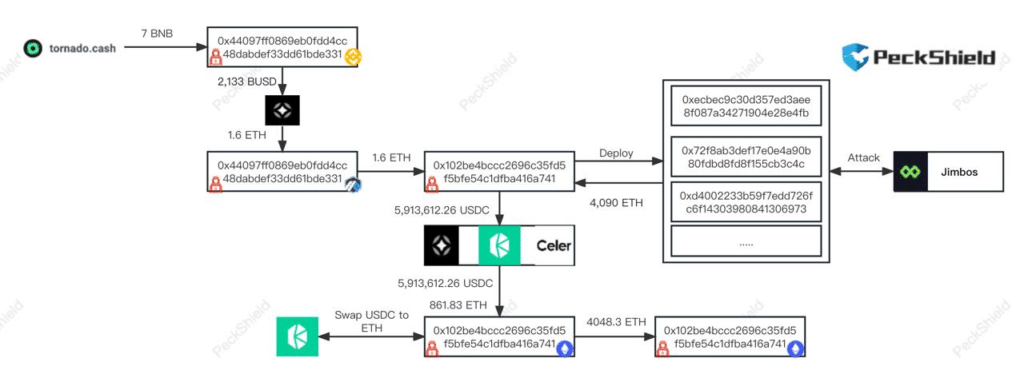
The flow of stolen funds on Jimbo and the hacker’s escape
After tampering with the price stability of the crypto protocol based on Arbitrum, the criminal used the Bridge Stargate to move the stolen 4090 ETH onto the Celer network.
Previously, the same individual had used the Tornado Cash mixer to extract the 1.6 ETH as seed cash with which to pay fees for his operations.
Tornado Cash is a privacy-focused protocol that allows its users to make their transactions untraceable by mixing their funds with those of other users on the platform.
After several transactions, the funds arrived at this address, where they are currently stored.
The following image provided by Peckshield shows us how the flow of crypto stolen by the attacker unfolded, who by the end pocketed 4048.3 ETH.
The Jimbos team, after realizing the capital leak, said on social media that it had contacted law enforcement and several teams of cybersecurity experts who have worked in past exploits at Euler Finance and Santiment.
It is worth recalling that all transactions occurring in crypto are publicly visible on the blockchain, despite common narratives from industry detractors describing them as impossible to trace.
Should the attacker stumble, for example, trying to sell stolen ETH for FIAT, he would be discovered by analysts breathing down his neck, and through the cooperation of the exchange in question he could be quickly identified.
A Web3 security expert user involved in the Jimbos support team on the news hinted that things could get ugly for the thief if he does not immediately return the funds
Crypto and cybersecurity: hacks don’t concern only Arbitrum
Unfortunately, hacks and exploits in the crypto world are commonplace and do not affect only the Arbitrum network, but the entire DeFi industry.
Despite the fact that several billion dollars are invested within a multitude of decentralized protocols, this type of finance, untethered from trusted intermediaries, is still an experiment in need of improvement.
In particular, the complexity of the smart contracts on which these marketplaces are based means that a single error in the code or bug can prove fatal and compromising to the entire project.
In May alone, counting the latest Jimbos hack, nearly $17 million was stolen, which at the end of the day constitutes a paltry sum compared to what was taken away by hackers and cyber thieves.
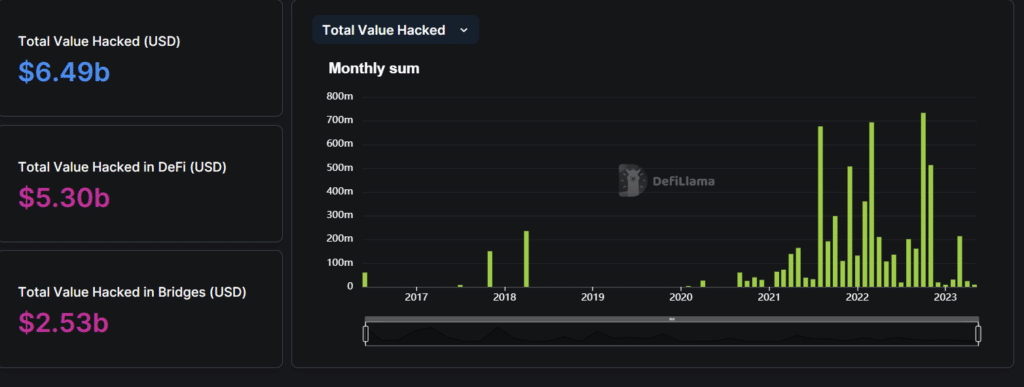
In fact, DefiLama‘s data show the total hacked since 2016 amounts to about $6.5 billion, with a record high of $782 million in October 2022.
The most affected niche in this context is bridges, which are highly vulnerable and full of flaws that have been punctually exploited by some malicious user.
About $2.5 billion have been taken away from bridges alone.
The hope for the years to come is that we can develop some sort of protection against cyber attacks, through spreading awareness about these issues and through stricter regulation of the DeFi world for crypto criminals.
Unfortunately, the evolution of technology and the creation of innovative applications includes these mishaps, which must be taken as lessons for the community to develop suitable security measures for the future.