On 28 March 2023, the security of Safemoon’s LPs was breached by a hacker attack, involving more than $8 million.
It appears that the Safemoon team is in contact with those responsible for the cryptocurrency theft, but the story may be hiding some dirt.
Let’s look together at the details of this most interesting affair.
Safemoon LPs victims of hacker attack: security cost $8 million
On 28 March 2023, the Safemoon team told the community that its LPs were compromised in a theft worth more than $8 million in crypto-assets.
The attack was made possible by a vulnerability in Safemoon’s contract associated with a feature called “Bridge Burn.”
This feature would have allowed the thief to transfer user tokens to the developer’s address.
The result was that 32 billion SFM tokens were sent from Safemoon’s LPs address (0x8e0301e3bde2397449fef72703e71284d0d149f1) to the deployer’s address (0x678ee23173dce625A90ED651E91CA5138149F590).
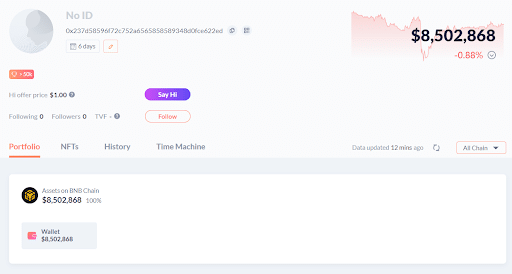
This brought an instantaneous price pump, which allowed the hacker to empty the LPs, swap all the SFM tokens to BNB, and transfer them to this address, in which they are still stored: 0x237d58596f72c752a65658589348d0fce622ed.
The address is only 6 days old, but can already count a balance of more than 27,380 BNB equivalent to $8.5 million.
The Safemoon team is in contact the perpetrators of the hacking attack
Apparently, the person responsible for the theft got in touch with the Safemoon team.
How? Quite simply through the additional data (intended as text) that can be added to each transaction made on blockchain.
The address used by the hackers to send the message to the Safemoon team is the following:0x286e09932b8d096cba3423d12965042736b8f850.
The message reads:
“Hey relax, we are accidently frontrun an attack against you, we would like to return the fund, setup secure communication channel , lets talk.”
The conversation continued until an unknown user sent a message to the Safemmon team through this address:
0x70b8172e628992007453aa4fe27048b59957e0ef
The message reads:
“Let me give you some advice: seek help from security companies that have good connections with Binance to obtain the hacker’s personal information and involve law enforcement.
Hackers may only refund the money when their safety is threatened, so it may be necessary to engage the underworld power in the hacker’s residence.
I assure you that this is the most effective approach. If you are not in the same country as the hacker (most likely China), seek help from the community. The Safemoon community could reach the hacker’s home in half a day.”
In a nutshell, the unknown user recommends relying on on-chain investigation companies that have a good relationship with Binance, this is because it was discovered that the address responsible for the theft had previous transactions with Binance, hence the cryptocurrency exchange is in possession of personal data thanks to “know your customer” (KYC) verification.
After discovering the hacker’s data and home address, the best strategy would seem to involve the authorities and take action, again according to the unidentified user’s report.
For now Binance has not issued any statement on the matter, we remain waiting to find out if there will be any news on the matter.
Safemoon hacker attack: what if the team was involved in the affair?
There are those who speculate that the Safemoon team is making the whole thing up and that they are responsible for compromising LPs.
In particular, a Dune user by the nickname “@factsudeny” posted an address involved in the theft that he said was related to Safemoon.
Cross-chain data show that these addresses match across different blockchains, though it is not yet possible to confirm this.
According to the Twitter community, this seems very strange:
Details of the attack show that the “bridge burn” function, which allegedly enabled the hacker attack on Safemoon LPs was implemented by the project’s developers on 28 March 2023 at 10:52 AM (UTC).
Several hours later, the attack took place.
In addition there is to consider that the previous version of the smart contract did not have these vulnerabilities.
Many believe that the Safemoon team is responsible for the attack
Someone has abused burn() function of #Safemoon new smart contract, gaining almost $9M
Not sure whether we can call it as a “hack”, but anyway that quite funny
Check the details in the thread

…
— hackenhacker.eth (@hackenhacker) March 29, 2023
How is the SFM token doing following the alleged hack?
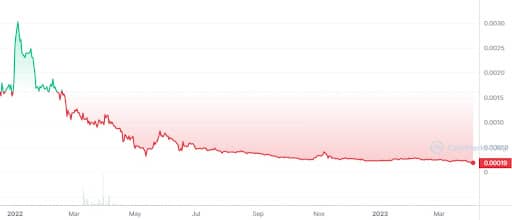
Today the SFM token appears to be recovering slightly with an increase in the last 24 hours of 4.3%. The current price is $0.000189 per token, market capitalization of $105 million and volumes in the last 24 hours hovering around $1 million. The price is far from its all-time high, which stands at $0.003 per token; this is a drawdown of more than 90%.
On 28 March, the day of the alleged hack, the SFM token suffered a sharp downward slide that took it from $0.000239 to $0.000190 in a very short time, a percentage change of -19%.
This situation may not have created major structural problems for the Safemoon token, given the strength and resilience of the community.
However, it is a must to remember that this is a highly speculative token, lacking any purpose of existence, and without any innovation in the blockchain field.
Moreover, it is important to note that the token was born in the wake of the success of memecoins during 2021: as of today Safemoon still lives but is far from its all-time high. There is a high risk that this project will disappear in the years to come and be replaced by new trends and innovations in technology.